Mozilla SOPS: Secrets OPerationS
I wrote a blog post about managing secrets in GitLab / Git some time ago, where I touched sops. Today, I am going to write more about this tool.
sops is useful when you want to encrypt your data and keep it somewhere securely. Why is it so secure? Because it uses envelope encryption. This way you can keep your encrypted data and encrypted data key (which is needed to decrypt your data) in the same file. So, when everything is encrypted you can store it anywhere, for example in your git repository.
How it works?
sops generates a data key and this data key is used to encrypt and decrypt your data. So, how then is your data key encrypted? 🤔 By your KMS or PGP master key (or both of them, or even more... sops supports AWS KMS, GCP KMS, Azure Key Vault and PGP).
As you can see, sops only touches your data key and your data. With your master/wrapping key you encrypt and decrypt your data key.
By default, you can encrypt and decrypt your data key by each master key. But, you can use key groups if you want to be more secure (sops uses Shamir's Secret Sharing algorithm under the hood to split the data key). Using key groups, sops splits data key into parts. Each key group encrypts and decrypts only a part of data key:
So, what is going on here? There are three key groups. Each of them encrypts and decrypts only a part of data key. In order to decrypt a file, you must decrypt data key firstly, and each key group can decrypt only a part of it. So, to decrypt the data key you have to decrypt all the parts (by default) and then merge them (it is not exactly merging, but you get the idea). Each master key in the key group can decrypt a part of the data key. So, in this example, in key group 1, you need to have access to only one of the master keys to decrypt this part of data key. The same is for another key groups. You only need one master key within each key group to decrypt this part of data key.
You can also create five key groups and set threshold to 3. This way, you only need access to any 3 key groups to decrypt a file (Shamir's Secrets Sharing algorithm).
As I wrote, key groups are optional and in most cases you do not need to use them.
Key rotation
If you think, that your data key leaked you can renew your data key; it is also a good practice to do that on a regular basis. Sops will create a new data key, and encrypt data with this new data key. You just need to type: sops -r file-with-secrets.yaml.
Examples
Okay, I think that you understand basics. Now let's see some examples.
First example
In the first example I am going to use my PGP key.
I added my fingerprint (from PGP key) to .sops.yaml file. This way I tell sops that I want to encrypt and decrypt data key with this master key. Sops encrypted the data key with my public key, and data in a file has been encrypted by data key. Only someone who has access to my private key can decrypt the data key, and then using this data key, the data can be decrypted.
Second example
In this example, I am going to use two PGP keys. Let's say that I'm working with someone and I have access to their public key.
Using two PGP keys, the same data key is encrypted two times (separately). Once by the public key of my colleague and once by mine. Thus, there are two records in sops.pgp section. To decrypt the file I only need my private key. The same way, if my colleague needs to decrypt the file, they only need their private key.
In this way, if I die (or lose my private key...), my colleague still will be able to decrypt the file. So, it is always a good idea to encrypt your data key with more master keys than one ☝️.
Third example
In this example, I am going to show you key groups. There will be three key groups with one master key in each of them.
Let's say that we have three developers. And, to decrypt the file we need at least two of them. I can set threshold to 2 (by default, it would be 3). So, in order to decrypt data key, we need at least two different developers (I assume that each developer has access to only his private key).
In this way, in order to decrypt the file there always must meet at least two developers. So, it might be useful when you have something very very secret 🤫. There is a limit for 256 key groups 😅.
Decryption
Okay, so I have the encrypted file. I can type sops example-secret.yaml and see the content. But, what if I want to use it in my scripts? And I need access to a specific key.
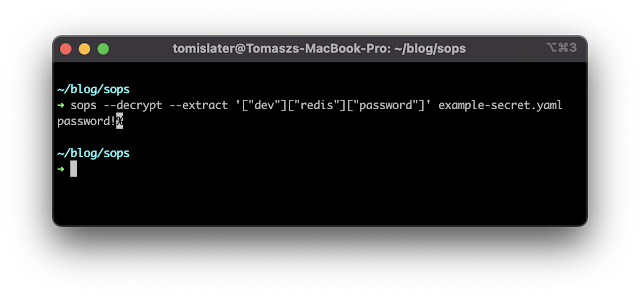
Let's say that I want to get a password for redis and put it to an environment variable. How can I do that? Firstly, I have to tell sops that I want to decrypt the file (--decrypt flag). Secondly, I need to provide what exactly I want to extract (--extract flag):
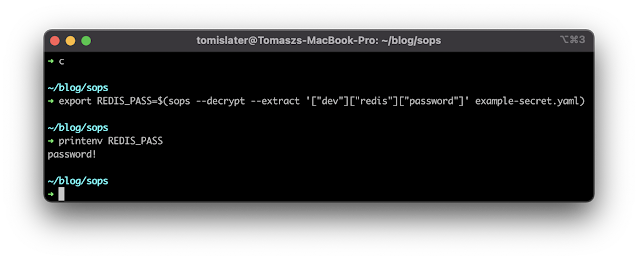
So, when I know how to extract a specific value, then I can put it to my environment variable:
And that's it! There is a lot more stuff you can do with sops of course. But, my goal in this post was to introduce this tool to you. And I hope, I achieved that. Let me know if it was useful!
And here is a video if you do not want to ready this post:






Comments
Post a Comment